Welcome to the Restate TypeScript + AWS Lambda template! ✨
- 📦 Node.js 22+ installed
- 🔧 npm or yarn package manager
- 🌐 AWS account (for deployment)
Install dependencies:
npm installLaunch the local Restate server:
npx @restatedev/restate-serverStart the local endpoint:
npm run devConnect your local service to Restate:
npx @restatedev/restate dep add http://localhost:9080Iterate! 🔧
This template includes a GitHub Actions workflow setup for automated deployment.
Before setting up the repository, create the AWS Lambda from the AWS console: https://docs.aws.amazon.com/lambda/latest/dg/getting-started.html. Then, you'll need two AWS roles to setup:
- The role to invoke, to configure in the Github actions secrets as
AWS_INVOKE_ROLE_TO_ASSUME - The role to deploy, to configure in the Github actions secrets as
AWS_DEPLOY_ROLE_TO_ASSUME
First, obtain the role to invoke the Lambda. To do so, visit the Restate Dashboard at Developers > Security > AWS Lambda. When configured, set it up in the Github actions secrets as AWS_INVOKE_ROLE_TO_ASSUME.
To set up the repository, you need to configure your AWS account for the Github OIDC provider.
Run:
aws iam create-open-id-connect-provider \
--url https://token.actions.githubusercontent.com \
--client-id-list sts.amazonaws.comNow you can create the deploy role. The role should have the following Trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<ACCOUNT_ID>:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"token.actions.githubusercontent.com:aud": "sts.amazonaws.com"
},
"StringLike": {
"token.actions.githubusercontent.com:sub": "repo:<GITHUB_ORG>/<GITHUB_REPO>:*"
}
}
}
]
}And the following permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "LambdaDeployPermissions",
"Effect": "Allow",
"Action": [
"lambda:GetFunctionConfiguration",
"lambda:CreateFunction",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration",
"lambda:PublishVersion"
],
"Resource": "arn:aws:lambda:<REGION>:<ACCOUNT_ID>:function:<FUNCTION_NAME>"
},
{
"Sid":"PassRolesDefinition",
"Effect":"Allow",
"Action":[
"iam:PassRole"
],
"Resource":[
"<AWS_INVOKE_ROLE_TO_ASSUME>"
]
}
]
}Once the role is configured, set it up in the Github actions secrets as AWS_DEPLOY_ROLE_TO_ASSUME.
For more info, check https://github.com/aws-actions/aws-lambda-deploy?tab=readme-ov-file#credentials-and-region
Finally, add the following to Github Actions repository secrets:
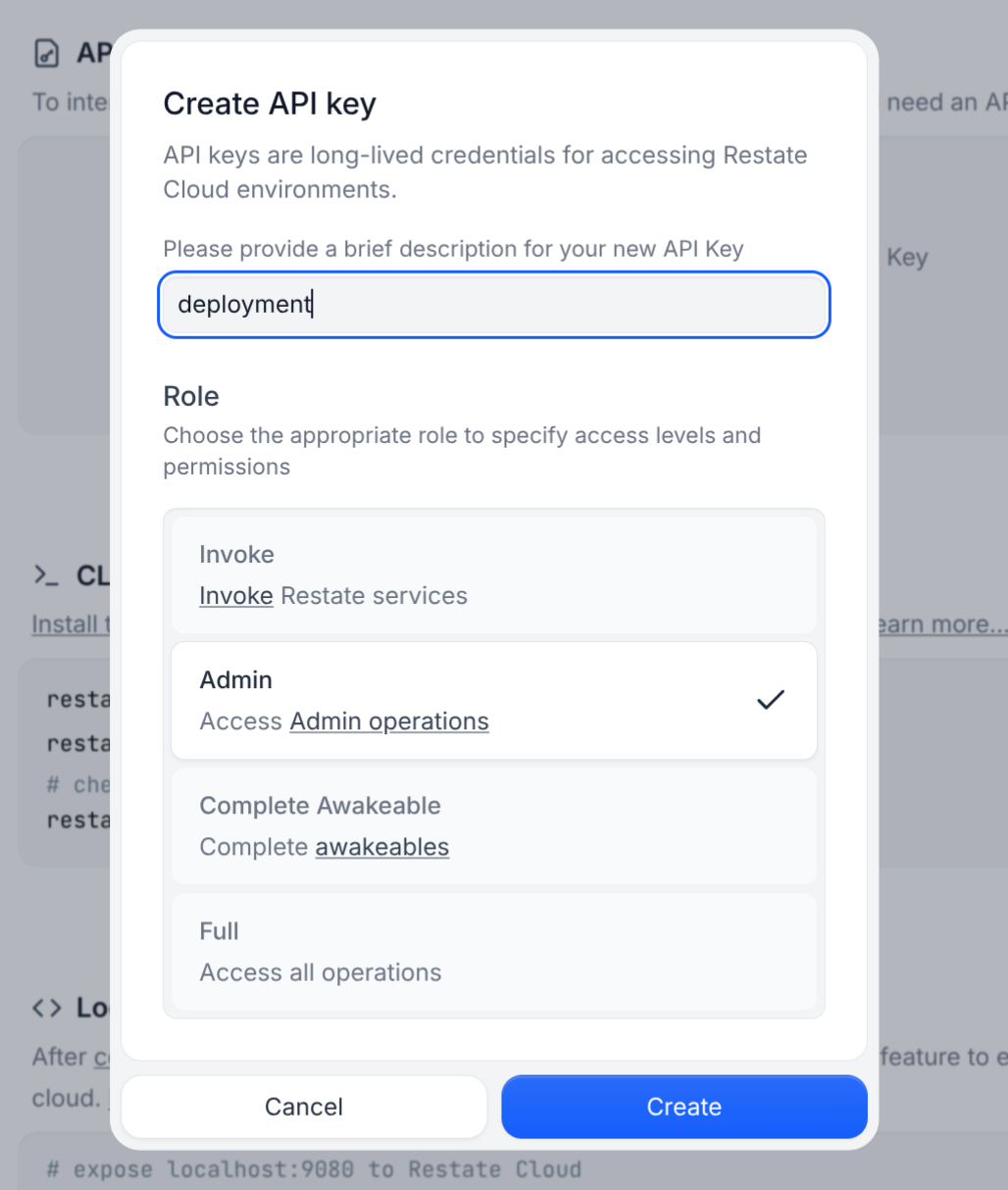
RESTATE_ADMIN_URL: The Admin URL. You can find it in Developers > Admin URLRESTATE_AUTH_TOKEN: Your Restate Cloud auth token. To get one, go to Developers > API Keys > Create API Key, and make sure to select Admin for role
Once the repo is set up, just push to the main branch and you'll get your services updated.
Check the workflow deploy.yml for more details.
You can create a zip ready to deploy on Lambda executing:
npm run bundleFor more info on how to deploy manually, check:
- For cloud: https://docs.restate.dev/cloud/connecting-services
- For on-prem Restate deployments: https://docs.restate.dev/services/deploy/lambda
- 📖 Explore the Restate documentation
- 🔍 Check out more examples and tutorials
- 💬 Join the Restate Discord community
Happy building! 🎉